| Forward | Subscribe |
 |
August 2016 |
|
| Get A Quote | My Website | Attorney Fees Brochure | Download vCard |
Hackers Use Mobile Devices to Break Through Data Security Walls
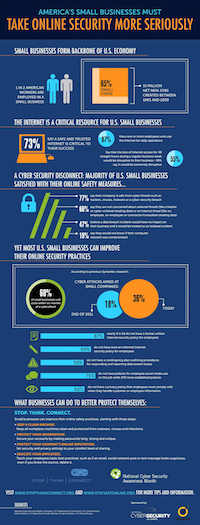 Small businesses are also under cyberattack. Click to expand.
Small businesses are also under cyberattack. Click to expand.Proliferation of Mobile Devices Multiplies Risk
Working against heightened efforts to lock down our cyberborders is the exploding use of mobile devices, especially by busy professionals. Not only are we doing more work away from the office, but we are using a growing variety of mobile devices to get that work done – including smart phones, notebooks, laptops and now even wearables. When these devices are not properly secured, which is too often the case, cybercrooks can easily evade enterprise-wide protections. Thus, mobile devices have become the weak link in the data security chain, according to many corporate IT officers, and are increasingly the launching pad for successful attacks.
Meanwhile, cyberthieves are using a rapidly expanding bag of tricks to take full advantage of the situation. Small, lightweight and portable, mobile devices are easy to steal or leave behind in a thousand different places. Once in hand, mobile devices (even those with tough security locks) can be defeated by a seasoned attacker and mined for corporate data or passwords. Hackers are also scamming users into downloading mobile malware with email, text messages and bogus advertising. And then there are Wi-Fi hackers who use easily obtained equipment to read a nearby wireless device or install malware that will allow future data access.
We Are the First Line of Defense
The first line of defense in this cybersecurity battle is, of course, those of us who depend on our mobile devices to help us do our jobs. Yet surveys show that many of us are unaware of the data security threats posed by our mobile devices and/or haven’t implemented available security measures. Here are eight tips from the Center for Internet Security to help you get started (download PDF for full details):
 |
| Click to expand. (Courtesy of the Center for Internet Security.) |
- Regularly update your device. Safeguard against the latest mobile malware by updating operating systems and security software as soon as updates are available.
- Enable encryption. This is one of the best ways to thwart unauthorized access to information stored on your device.
- Use a passcode. Why make it easy if your device falls into the wrong hands? Create a strong, unique password, don’t share it with others, and enable authentication after a period of inactivity.
- Do not use public Wi-Fi. Don’t log into accounts and manage any sensitive transactions while using public Wi-Fi. Also disable the “automatically connect to Wi-Fi” setting.
- Install applications only from trusted sources. Many applications fail security tests, so check online reviews for security warnings before downloading.
- Install a phone locator/remote erase app. If your phone already has this app, turn it on.
- Disable certain services when not in use. Turn off services like Bluetooth and Near Field Capabilities (NFC) when not in use to prevent unauthorized access by a nearby user.
- Carefully dispose of mobile devices. Make sure you wipe information from your smartphone and other devices before disposal. Check the manufacturer's website for instructions.